What are Cybercrimes? Types and Safety Tips.
Over 100 people fall prey to cyberattacks every hour!
Primarily, it’s investment scams that defraud the most money out of the general public, but there are other internet traps too, such as tech support scams, honey-trapping, spoofing, and whatnot.
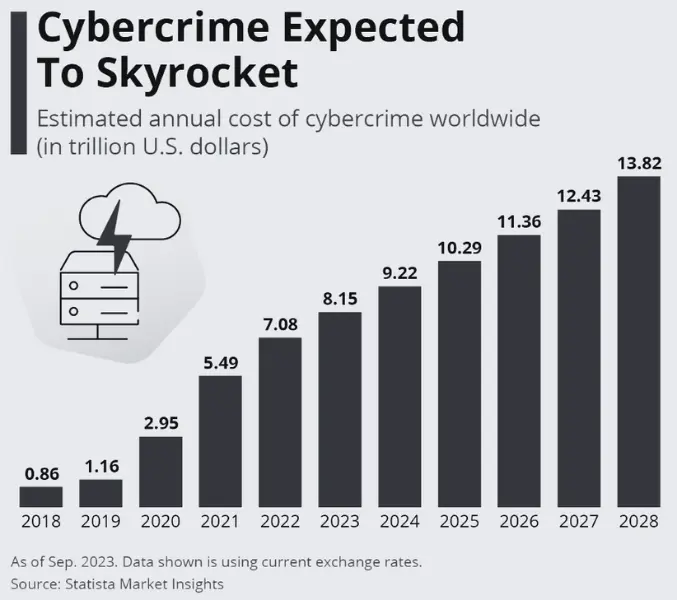
As internet and device penetration rise, cybercrimes have become a thriving “industry”–growing at an exceptional CAGR year on year.
For context, the financial scale of cybercrimes has surpassed the GDP of every other country except the USA and China since 2021.
Types of Cybercrimes
Here’s a list of major cybercrime categories for individuals and how to avoid being a victim.
1. Phishing
- Modus Operandi: This starts with a safe-looking email or message that appears to come from a trusted source. It takes the victim to a fake replica of a legitimate website or internet portal, tricking a victim into revealing sensitive information such as their online banking credentials, social login details, credit card numbers, and more.
- How to Stay Safe: Never click links that you don’t trust. If unsure, copy-paste the link into a search engine like Bing or Google and see what comes up. Make sure the sender is actually the one you think. Double-check the domain sending the email/message and confirm with the service provider about its authenticity.
2. Malware
- Modus Operandi: User’s computer gets infected by visiting shady websites or installing files downloaded from untrustworthy sources or rogue email attachments. Based on the type of malware, it can infect files (virus), lock a user out of their own computer (ransomware), leech resources indefinitely (cryptojacking), disrupt routine activities with ads (adware), keep tabs on user activities (spyware), etc.
- How to Stay Safe: Never download anything from non-reliable websites. Respect browser warnings. Install reputed 3rd-party antivirus. Turn on the on-device protection at the very least.
3. Social Engineering
- Modus Operandi: Cybercriminals, imposing as someone in authority, manipulate individuals into revealing sensitive information, granting access to restricted systems, or doing something you won’t otherwise. This exploits basic human instincts like fear, greed, and trust.
- How to Stay Safe: Trust your gut and learn to say NO. Don’t concede to pressure. Buy time, and talk to your peers to have a second opinion. Contact (if possible, physically) the head office of the concerned “official” or “service provider” to confirm their legitimacy.
4. Online Harassment
- Modus Operandi: The scammer uses any telecommunication or social media, to follow, intimidate, or harass the victim. It may include threatening messages, spreading false information, or plain simple stalking. Often, the criminal is someone known to the victim (former colleague or partner, neighbor, classmate, etc.), but it can also be a complete stranger in some cases.
- How to Stay Safe: Don’t engage with the scammer. Document everything, stay vigilant, and inform law administration without any delay.
We have taken the onus upon ourselves to make aware and empower internet users against those growing cyber threats. And the first step is to have the right information about what’s actually happening.
Sign up for our newsletter to get those crucial details delivered to you, twice–every month.
